
A vulnerability assessment is a crucial part in every penetration test and is the process of identifying and assessing vulnerabilities on a target system. In this part of the tutorial we will be assessing the vulnerabilities available on the network side of the Metasploitable 2 virtual machine. We will be assessing the web applications on the Metasploitable 2 machine in a later tutorial. In the previous Metasploit enumeration and fingerprinting tutorial we’ve learned that the Metasploitable 2 machine contains a lot of vulnerabilities. We have collected valuable information about the target system which we will be using to find known vulnerabilities both on- and offline. Exploitation of these vulnerabilities will be demonstrated in the next exploitation tutorial. In this tutorial we will be looking at a few different ways to perform vulnerability analysis. We will be manually searching for exploits, use scanning tools like Nmap with scripts and we will be looking at the use of automated vulnerability scanners like Open-Vas. Each scanning technique and method has its own advantages and disadvantages as we will learn later on in this tutorial.
As mentioned before there are many ways to perform vulnerability analysis, from manually searching through exploit database to fully automatic testing with tools like Open-Vas and Nessus vulnerability scanner. Vulnerability scanning with automated tools is a very aggressive way of vulnerability scanning as it takes a lot of requests and traffic to complete this kind of scans. In some cases the great deal of traffic might crash (DOS) target hosts and services so it is advised to be careful when using these kind of tools. Beware to only use these vulnerability scans on hosts which you have permission to scan. When you are using automated tools for vulnerability scanning it is always wise to use multiple tools to rule out false positives. Therefor it is important to also master the manual ways of vulnerability analysis and do not become too reliant on automated scanners.
Metasploitable 2 enumeration information
Let’s start this vulnerability assessment by looking what we already know about the Metasploitable 2 machine from the previous enumeration phase.
- It is running Linux 2.6.9 – 2.6.33 as an operating system.
- The server name is METASPLOITABLE.
- There are 35 user accounts available.
- The msfadmin is the administrator account.
- There is no expiry date on the password of the msfadmin administrator account.
- We know which services are running, the versions of these services and on which port they are listening.
- There is a webserver and SQL server running on the Metasploitable machine.
From the Nmap service scan we got the following details about open ports and services:
| Service | Port | Status |
| Vsftpd 2.3.4 | 21 | Open |
| OpenSSH 4.7p1 Debian 8ubuntu 1 (protocol 2.0) | 22 | Open |
| Linux telnetd service | 23 | Open |
| Postfix smtpd | 25 | Open |
| ISC BIND 9.4.2 | 53 | Open |
| Apache httpd 2.2.8 Ubuntu DAV/2 | 80 | Open |
| A RPCbind service | 111 | Open |
| Samba smbd 3.X | 139 & 445 | Open |
| 3 r services | 512, 513 & 514 | Open |
| GNU Classpath grmiregistry | 1099 | Open |
| Metasploitable root shell | 1524 | Open |
| A NFS service | 2048 | Open |
| ProFTPD 1.3.1 | 2121 | Open |
| MySQL 5.0.51a-3ubuntu5 | 3306 | Open |
| PostgreSQL DB 8.3.0 – 8.3.7 | 5432 | Open |
| VNC protocol v1.3 | 5900 | Open |
| X11 service | 6000 | Open |
| Unreal ircd | 6667 | Open |
| Apache Jserv protocol 1.3 | 8009 | Open |
| Apache Tomcat/Coyote JSP engine 1.1 | 8180 | Open |
Many of these services contain known vulnerabilities which can be exploited. The following step is to find out which services are vulnerable and collect information about how they can be exploited. There are several sources which can be used to determine if a service is vulnerable or not. The most popular and knows sources are exploit-db from Offensive Security and the Open Source Vulnerability Database (OSVDB). We will also be looking at searchsploit, an offline exploit database included with Kali Linux. Searchsploit is a great offline source when performing a vulnerability assessment as it contains a lot of information about known vulnerabilities and exploit code.
Since this is a hacking tutorial to teach you how to perform a vulnerability assessment and not a Metasploitable 2 hacking walkthrough guide, we will only assess a few vulnerable services. The remaining vulnerable services on Metasploitable 2 can be used by you to practice on. If you get stuck at some part do not hesitate to contact us by using the comment function at the bottom of this tutorial. Let’s continue this tutorial and vulnerability assessment with assessing the first running service we’ve discovered in the last enumeration tutorial; Vsftpd 2.3.4.
VSFTPD v2.3.4 vulnerabilities
To determine the vulnerabilities in the VSFTPD v2.3.4 service we will consult several resources. When we search Google for known vulnerabilities for this service it comes up with a known backdoor that was introduced in a download of the software in version 2.3.4:
This means that only a part of the VSFTPD v2.3.4 installations will be vulnerable since the back door was added after the release and have been removed from the software a couple days later. Nevertheless it will be worth a try to see if the installation on the Metasploitable 2 machine is vulnerable. There is also a Metasploit module available to exploit this vulnerability which we will be looking at in the next Metasploit exploitation tutorial.
CVE: CVE-2011-02523
OSVDB: 73573
VSFTPD v2.3.4 Nmap script scan
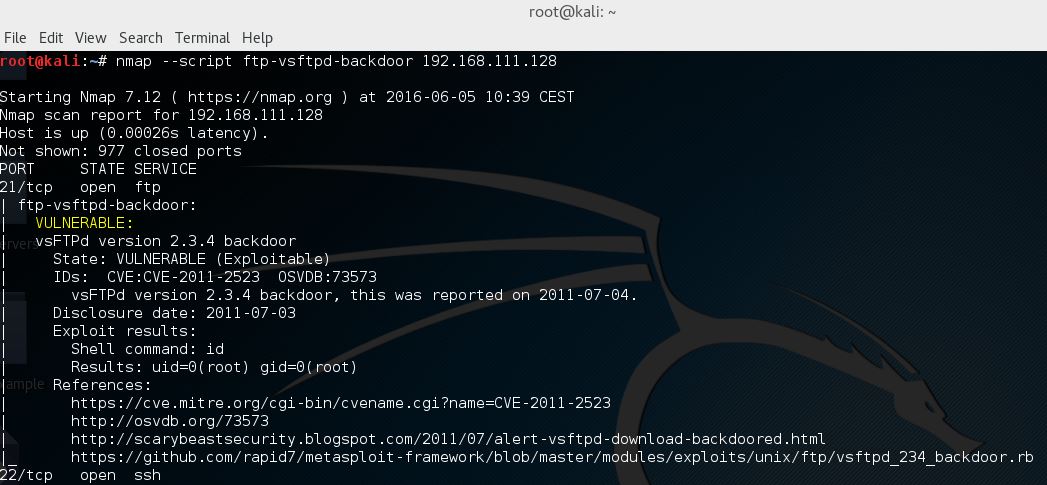
We could be firing up Metasploit and see if the service running on the Metasploitable 2 machine is vulnerable but there is another way. To determine if the FTP service contains a backdoor without actually gaining a shell we can use an Nmap script. Nmap script ftp-vsftpd-backdoor tests the VSFTPD v2.3.4 installation for the backdoor. Let’s start Nmap and scan our target host using the following command:
nmap --script ftp-vsftpd-backdoor –p 21 [target host]
And have a look at that, the Nmap script determined the running vsFTPd service to be vulnerable: More information about the Nmap script and additional script arguments can be found here: https://nmap.org/nsedoc/scripts/ftp-vsftpd-backdoor.html
More information about the Nmap script and additional script arguments can be found here: https://nmap.org/nsedoc/scripts/ftp-vsftpd-backdoor.html
 More information about the Nmap script and additional script arguments can be found here: https://nmap.org/nsedoc/scripts/ftp-vsftpd-backdoor.html
More information about the Nmap script and additional script arguments can be found here: https://nmap.org/nsedoc/scripts/ftp-vsftpd-backdoor.htmlUnreal ircd vulnerabilities
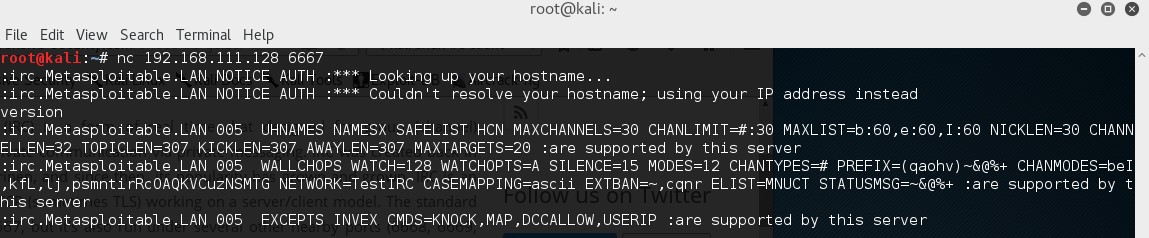
Let’s have a look at the Unreal ircd service, a known IRC service supporting many platforms. The only thing we know about this service until now is that it’s running on port 6667 from the Nmap scan. We do not know any further details such as a version number which would help us a lot in determining it’s vulnerabilities. A common method to determine the version of a service is by using a banner grabbing technique. Netcat is a tool which can be used for this purpose (among many other purposes). Let’s see if we can grab a banner using Netcat:
nc [target host]6667
Unfortunately there is no banner returned to us when we connect to the IRC service with Netcat:
 Let’s return to Nmap and use the following command to trigger a full scan on port 6667:
Let’s return to Nmap and use the following command to trigger a full scan on port 6667:nmap –A –p 6667 [target host]
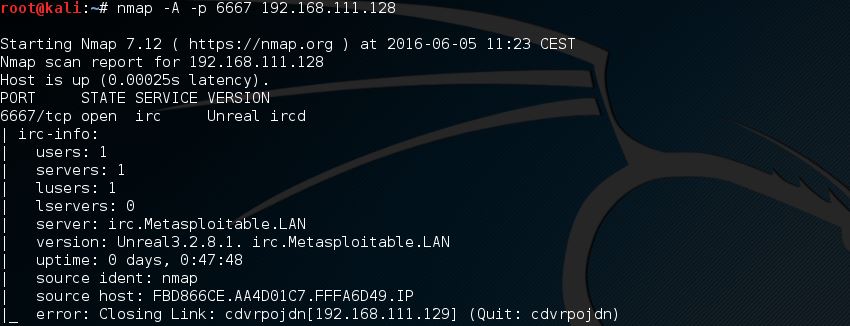 Nmap does return us the version number of the unreal ircd service which seems to be unreal ircd 3.2.8.1. When we search Google for the version number we quickly find that this version may contain a backdoor: https://www.rapid7.com/db/modules/exploit/unix/irc/unreal_ircd_3281_backdoor
Nmap does return us the version number of the unreal ircd service which seems to be unreal ircd 3.2.8.1. When we search Google for the version number we quickly find that this version may contain a backdoor: https://www.rapid7.com/db/modules/exploit/unix/irc/unreal_ircd_3281_backdoor
There is also a NMap script available for scanning the target hosts for the trojaned version of unrealircd. Use the following command to have Nmap scan the target host:
nmap –sV –script irc-unrealircd-backdoor –p 6667 [target host]
The output of the scripts states if the target host is probably vulnerable or not. The script issues a command on the target hosts but since there is no way to return the output of the command to our terminal session, we cannot be a 100% sure that the host is vulnerable using the script in this manner. In the following tutorial we will be looking at a few different ways of exploiting this vulnerability using Metasploit, NetCat and this Nmap script with additional script arguments.
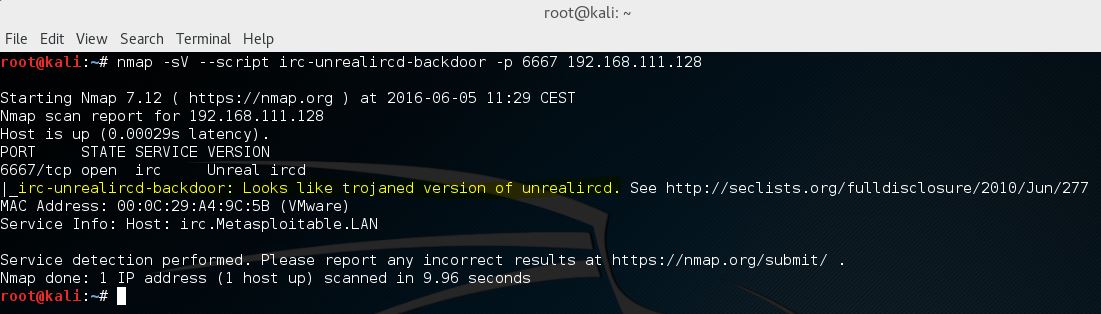 So far we are not a 100% sure if the unreal IRCD 3.2.8.1 service is vulnerable, we can only suspect it is.
So far we are not a 100% sure if the unreal IRCD 3.2.8.1 service is vulnerable, we can only suspect it is.Vulnerability assessment using Exploit Database
Another great source for finding known vulnerabilities is the Exploit database maintained by Offensive Security. Exploit-db offers a huge amount of exploits details, papers, shellcodes and can be searched using CVE and OSVDB identifiers. When we search the exploit database for the vulnerable backdoored version of Unreal IRCD there are several exploits returned:
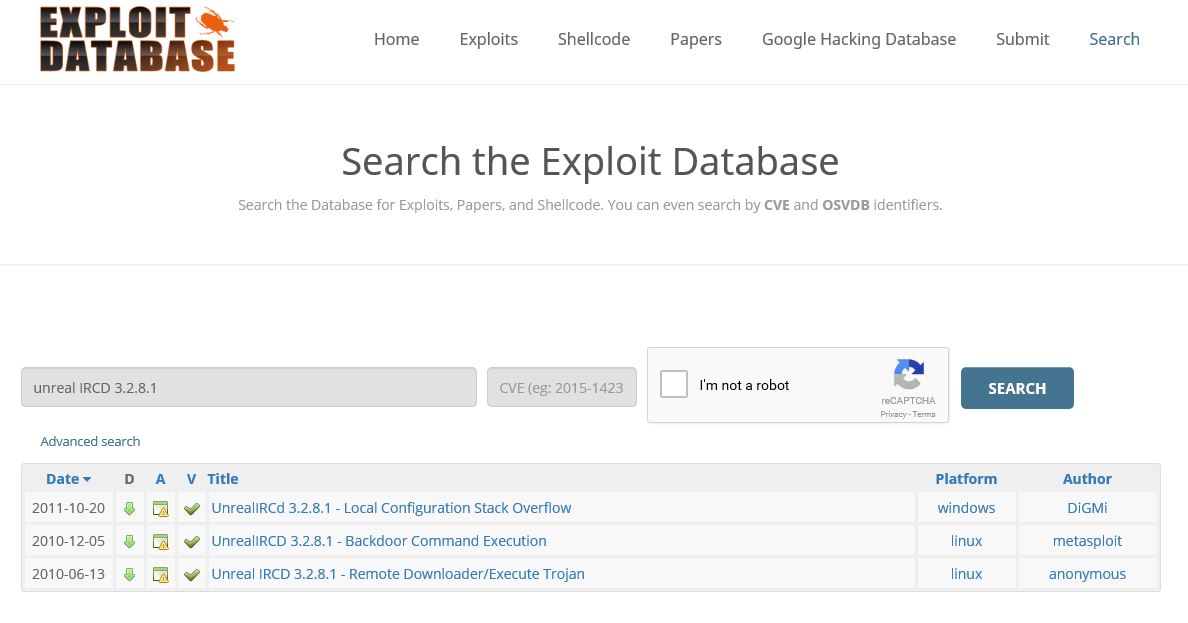 This version of unreal IRCD for Linux seems to contain multiple vulnerabilities:
This version of unreal IRCD for Linux seems to contain multiple vulnerabilities:
CVE: 2010-2075: https://www.exploit-db.com/exploits/16922/
CVE: 2010-2075: https://www.exploit-db.com/exploits/13853/
The first row is a vulnerability which only targets the Windows operating system, this one is not usable for the the Metasploitable 2 Linux machine. When we click on the found vulnerabilities we can download the exploit code to exploit the vulnerability. Often Exploit-db also contains a vulnerable version of the software for download which can be used for testing purposes in a controlled environment.
The exploit code is often written in programming languages such as Ruby (Metasploit modules), C, Perl or in Python. Please note that the offered exploit code often needs small modifications to successfully use the exploit against a target. This requires you to have at least some programming knowledge and experience to be able to modify the code. Many security researchers want to avoid that anyone (read: script kiddies) can use the exploit code out of the box without any prior knowledge of the subject and often only supply proof of concepts (POC). Of course this does not apply when there is a Metasploit module available which can be used out of the box without any modifications.
Be careful with downloading exploits!
Be careful when you are downloading exploits from other resources than Exploit-db. Exploits may contain malicious encoded shell codes which may harm your system, privacy or integrity. To avoid this kind of unexpected behaviour it is advised to audit the code and see if it functions as advertised. For example when you encounter a remote exploit that does not use network sockets, it is probably not a remote exploit and you should be careful compiling and running it. A little while ago I encountered an Apache exploit that was advertised as a zero-day exploit for the latest version of Apache which has not been patched. Analysing the code and the shellcode turned out that the exploit code only checks the current account privileges and contained shellcode to erase the entire hard drive.
CVE Databases
Another great source to search for vulnerabilities and information is the CVE database. The database can be searched using the following link:
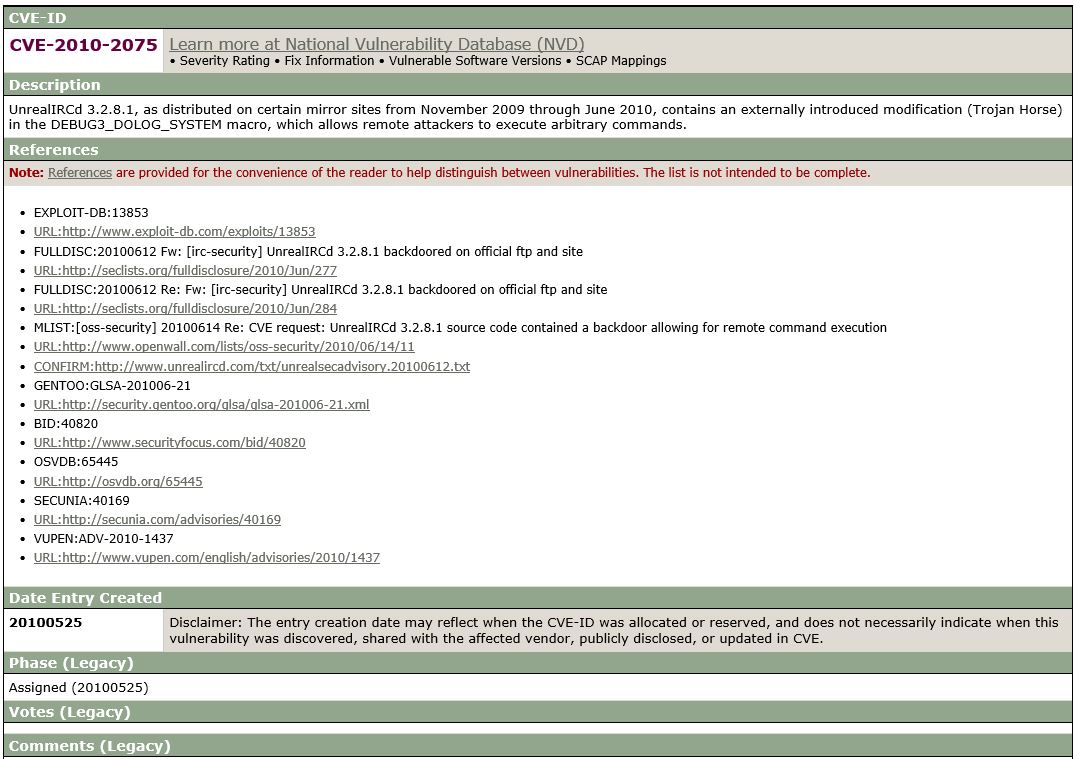
CVE Mitre
When we run a search for the CVE 2010-2075 vulnerability we can find a list of sources with full disclosures reports and some more links to information which might help us to get a better understanding of the vulnerability and how to exploit it.
Another great source for vulnerability assessments is the CVE details website. We can search this database for specific software and services to determine if they contain any known vulnerabilities. When we run a search for Proftpd 1.3.1 we find a bug list of known vulnerabilities which apply to this specific version. Including some vulnerabilities with a severe risk rating with a low complexity:
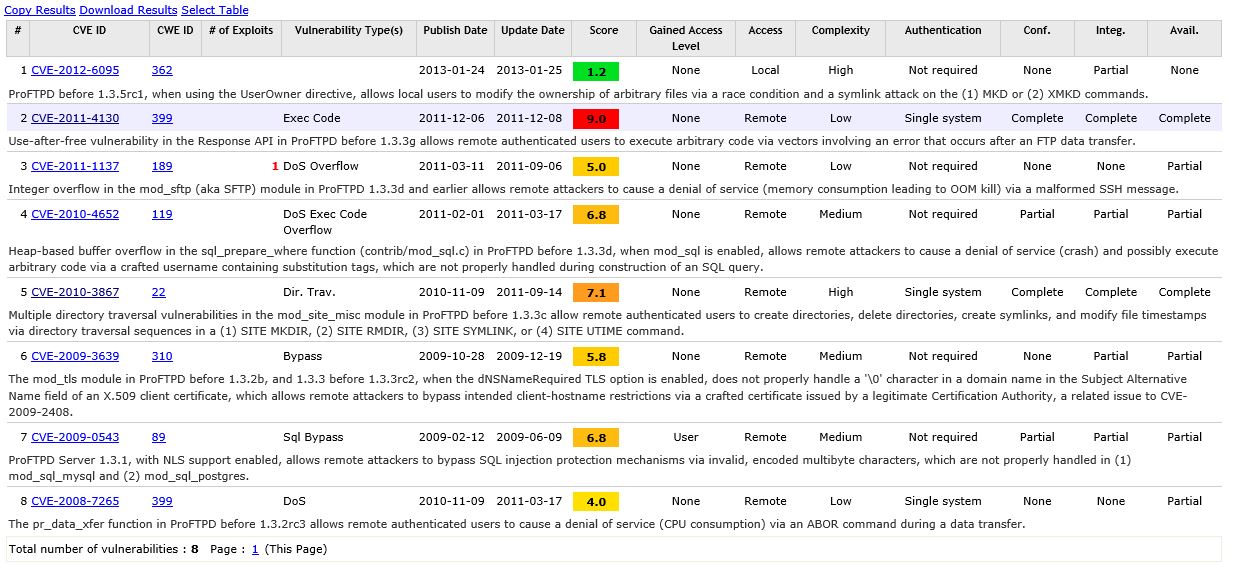
Source: CVEdetails.com
Searchsploit on Kali Linux
Another great (offline) source for finding vulnerabilities and exploits is searchsploit. Searchsploit is included with Kali Linux by default. Use the following command to search for unreal ircd vulnerabilities using searchsploit:
searchsploit unreal ircd
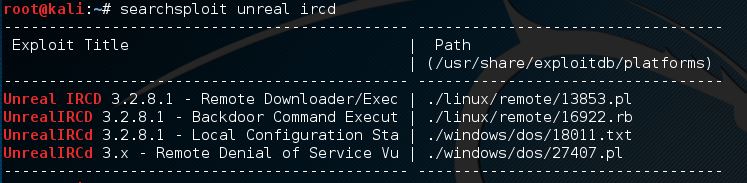 We can than print the contents of the files to the terminal using the cat command:
We can than print the contents of the files to the terminal using the cat command:cat /usr/share/exploitdb/platforms/linux/remote/16922.rb
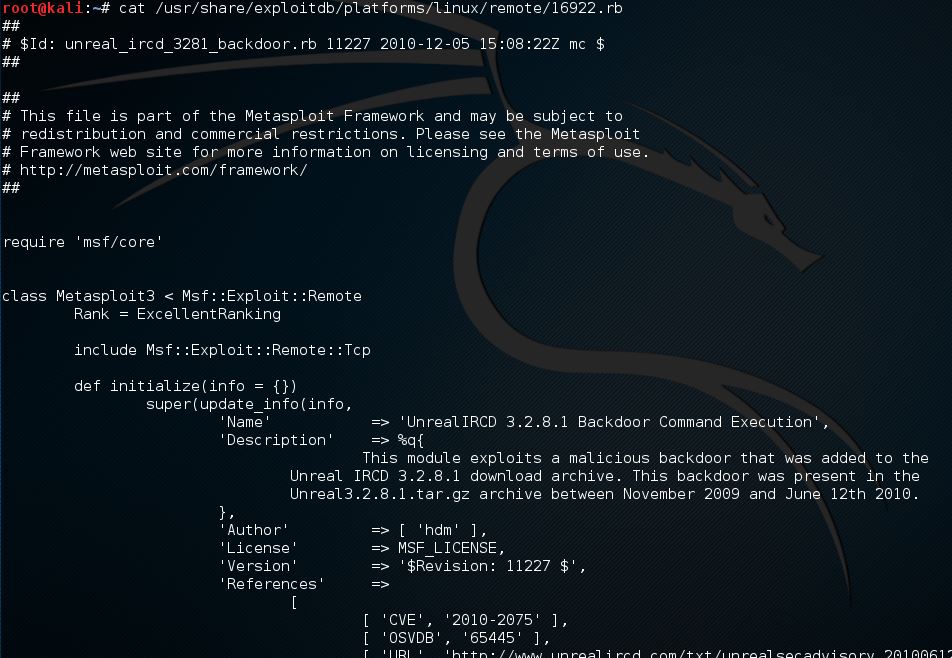
Sample of the Ruby exploit code used by Metasploit.
Open-Vas vulnerability scanner
So far we’ve only used Nmap and manual techniques to discover known vulnerabilities for our vulnerability assessment. There are other ways to rigorously test a host for vulnerabilities using highly automated vulnerability scanners such as Open-Vas and Nessus. Please be aware that using these scanners will generate a lot of traffic and may even DOS a target. Also use these type of scanner on hosts you physically own yourself or with a written permission to scan as it may be illegal to do otherwise.
It is beyond the scope of this tutorial to go into details about the installation process of Open-Vas. Follow this Open-Vas installation tutorial to install OpenVAS on Kali Linux. If you have problems installing Open-vas or running it, drop a comment below this tutorial and we’ll try to help you out as soon as possible.
After we’ve ran the Open-Vas vulnerability scanner, which may take a long time to complete, we’ve can have a look at the results below:
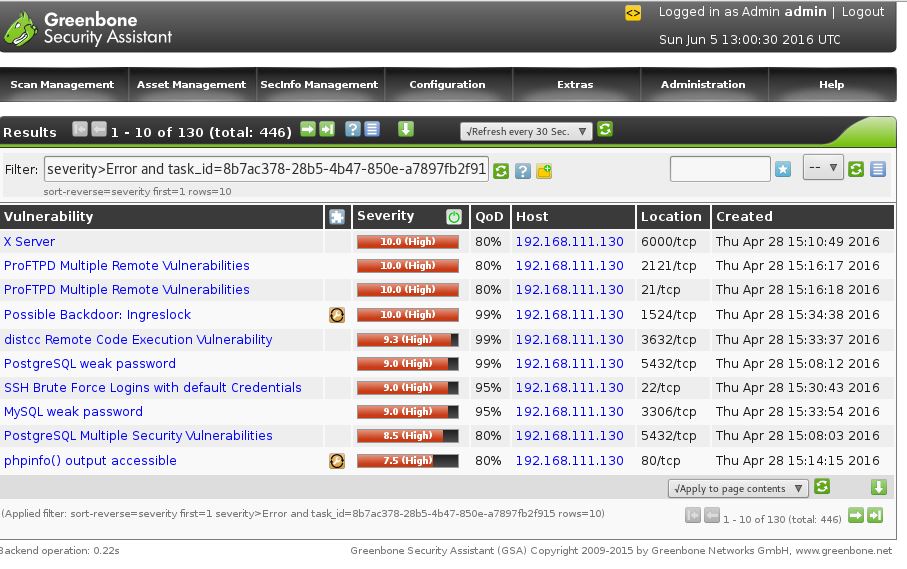 The results have been sorted on severity and as you can see Open-Vas has detected a lot of severe vulnerabilities. It is wise to use multiple vulnerability scanners in order to rule out false positives which may occur frequently during automatic vulnerability scanning.
The results have been sorted on severity and as you can see Open-Vas has detected a lot of severe vulnerabilities. It is wise to use multiple vulnerability scanners in order to rule out false positives which may occur frequently during automatic vulnerability scanning.Summary
So far our vulnerability assessment discovered a lot of vulnerabilities on the Metasploitable 2 machine for only 2 services using different techniques. Both the unreal ircd and proftpd services contain backdoors which can be easily exploited both manual and with Metasploit. We’ve also looked at the Open-Vas automatic vulnerability scanner and noticed a lot of severe vulnerabilities. In the next tutorial we will be exploiting the discovered vulnerabilities both manual and with Metasploit.

0 comments:
Post a Comment