
In this tutorial we will demonstrate how to install Metasploitable 3 in a Windows 10 environment using Vagrant, Packer and Virtualbox. So far we did a number of tutorials on hacking the Metasploitable 2 Linux machine on Hacking Tutorials. We’ve demonstrated how to install Metasploitable 2, how to enumerate it and perform a vulnerability assessment, and finally how to exploit it. As like many vulnerable machines that are for download Metasploitable 2 is a Linux machine. Because of strict licensing policies it a challenge to provide vulnerable Windows machines without breaking any licensing rules. Unfortunately you cannot just download the VM but you have to configure it yourself using a few tools and a Windows 2008 evaluation copy which is downloaded from the Microsoft website.
The installation process is pretty straightforward and should not cause too much trouble when the right dependencies are installed. The biggest part of the installation process is handled automatically by the install scripts. The full installation procedure might take a couple hours in total, be prepared to spend time on the installation of Metasploitable 3.
Before we can continue with the installation procedure we need to install a few dependencies:
- Packer v1.0.0: https://www.packer.io/downloads.html
- Vagrant 1.9.1: https://releases.hashicorp.com/vagrant/1.9.1/
- Vagrant Reload Plugin v0.0.1: https://github.com/aidanns/vagrant-reload
- Virtualbox 5.1.14: https://www.virtualbox.org/wiki/Downloads
In order to avoid (a lot of) trouble it is recommended to download the exact version as mentioned above. The success rate of the installation script depends greatly on the build environment. For your reference, we’re building the Metasploitable 3 machine on Windows 10 Enterprise x64 Build 15063.
Before we can build the VM we have to install Vagrant and Virtualbox using the downloaded installation files. We will not demonstrate the installation procedure for this software as it’s very straightforward and only involves clicking ‘next’ a couple times. Next we need to install the Vagrant reload plugin and we need to download Packer.
Install Vagrant reload plugin
Change the directory on the command line to the directory where you have downloaded and unpacked the Vagrant Reload plugin. Then run the following command to install the plugin:
vagrant plugin install vagrant-reload
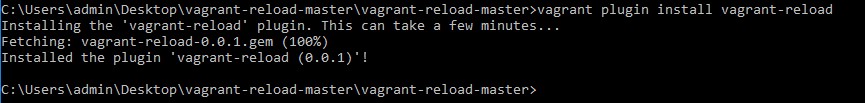
Vagrant plugin vagrant-reload successfully installed.
Now that we have installed the Vagrant reload plugin we can continue with downloading Packer.
Download Packer
The next step is to download Packer from the following download page:
Download the latest version of Packer and unpack it the Metasploitable 3 master directory. Storing the Packer binary in the Metasploitable 3 directory allows us to easily execute it to setup the VM without setting up system variables or using full paths to the binary. After copying the Packer file to the Metasploitable 3 directory we can start setting up the virtual machine.
Creating the Metasploitable 3 VM
Now that we have all pre-requisites installed we can use Packer to setup the Virtual Machine in Virtualbox. Move the command line to the Metasploitable 3 location and run the following command from an elevated command line:
packer build windows_2008_r2.json
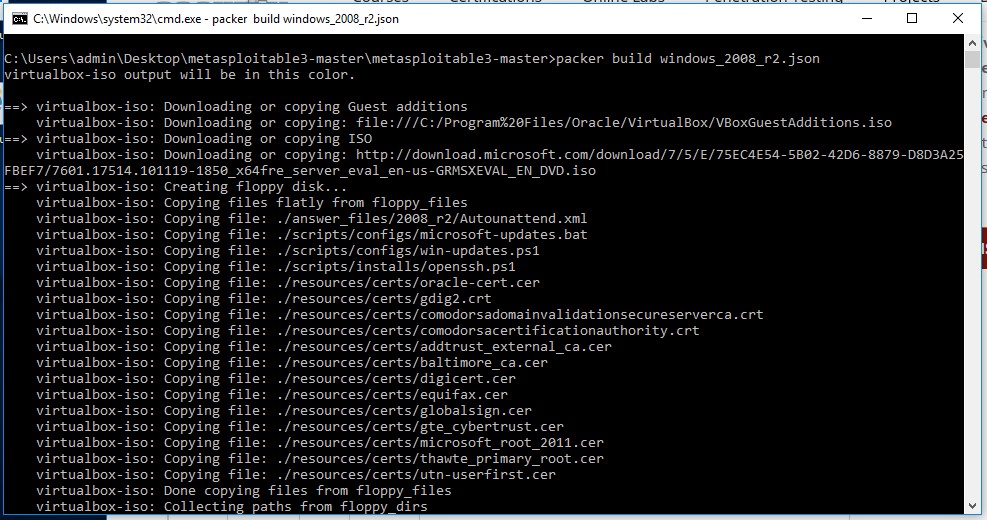
Building the Metasploitable 3 VM will take a while.
This command will take a while to complete because first it will download a Windows 2008 evaluation copy from the Microsoft website. When the download is finished, the script will continue to setup the virtual machine in Virtualbox and install Windows 2008 on the virtual machine. The entire process will take anywhere from 30-60 minutes. This depends on the configuration of your host machine and the speed of your internet connection. When the script is finished the output looks as following:
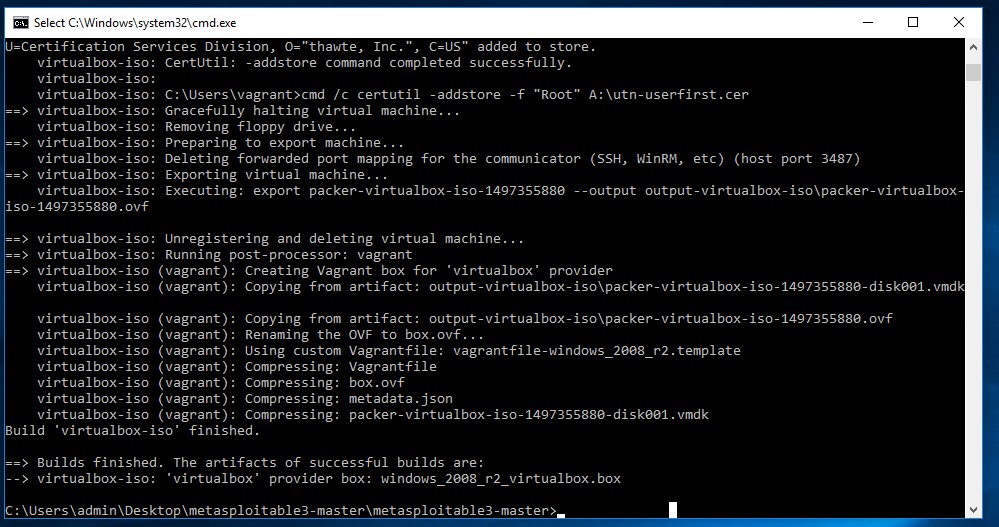
Metasploitable 3 build process finished without errors.
When the script is finished run the following command:
vagrant box add windows_2008_r2_virtualbox.box --name=metasploitable3
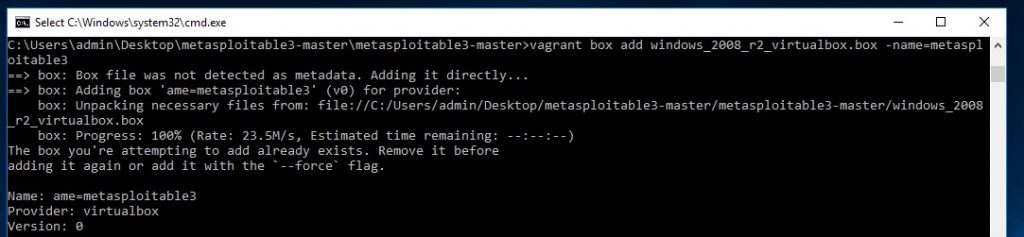
Metasploitable 3 added to the Vagrant environment.
Finally we have to run the one more command to have Vagrant execute the scripts that install the vulnerable software on the Windows server 2008 virtual machine. Run the following command and expect to wait another 15-30 minutes until completion:
vagrant up
This will conclude the installation of Metasploitable 3 and you should be able to start the VM within Virtualbox.
Metasploitable 3 installation errors with Vagrant
The Metasploitable 3 setup process is a bit tricky and prone to errors related to specific versions of the prerequisites. Most errors I faced while writing this tutorial were avoided by using the versions of Vagrant, Packer & Virtualbox mentioned earlier in this tutorial. Especially the latest version of Virtualbox resulted in many errors after issuing the vagrant up command.
During the installation of the vulnerable software you might get an error related to the virtual machine state: “The guest machine entered an invalid state while waiting for it to boot.”. When this happens reboot the virtual machine and run the vagrant up command again.
Another error that may occur during the installation of vulnerable software is the following: “chocolatey is not recognized as an internal or external command”. The error didn’t only apply to Chocolatey but also some other scripts. To get rid of this error I’ve added the following directory to the Path variable:
C:\Users\admin\Desktop\metasploitable-3-master\metasploitable-3-master\scripts\installs\
This will make all the scripts in this directory accessible without using a full path. Eventually I had to run the ‘Vagrant up’ command several times before it finished without errors.
Running Kali Linux VM on the same host
If you’re running your Kali Linux virtual machine in Virtualbox on the same host you have to make sure that you set the correct network settings. Otherwise you won’t be able to connect to the Metasploitable 3 machine from your Kali Linux attack box. You’re not required to alter the network settings for the Metasploitable 3 machine, only for the Kali Linux VM:
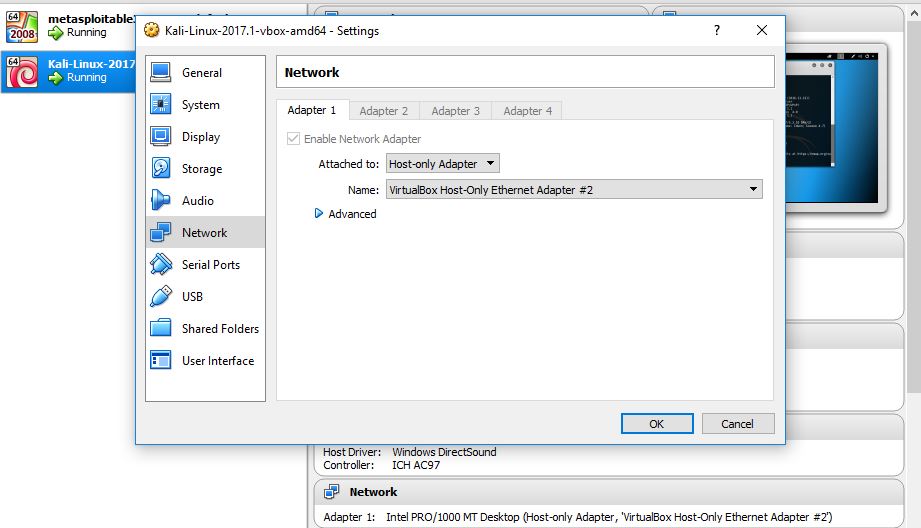
Choose: Host-only adapter.
Booting Metasploitable 3
Now that we’ve completed the installation procedure for Metasploitable 2 we are ready to boot in in Virtualbox. The default username for the virtual machine is “vagrant” with password “vagrant”. Even though the installation process produced quiet some errors there were none that we couldn’t fix quickly (Google is your friend!). I must say that the developers of Metasploitable 3 did a great job on the installation procedure and providing a vulnerable Windows machine to the public.

0 comments:
Post a Comment