In this new Metasploit tutorial we will be installing and configuring Metasploit on Kali Linux and the Metasploitable 2 virtual machine on VMware Player. Metasploit is one of the most popular and top rated penetration testing tools on the market and is designed for penetration tests, vulnerability assessments and developing and executing exploit code against remote targets. Metasploit is an open source project available in a free Metasploit Framework and community version and there is a paid pro version which even contains more features. Metasploit has several user interfaces, both command line and graphical user interfaces. Armitage is the graphical attack management tool which visualizes targets and is recommending exploits for known vulnerabilities. In this tutorial and the ones to following, we will be using the free Metasploit framework edition which is installed by default on the latest version of Kali Linux. If you have no or little experience with command lines and Metasploit we recommend you to read the Metasploit commands tutorials as well.
When you need to learn how to swim you need a swimming pool and when you need to learn how to hack you need vulnerable machines to practice on. Metasploitable 2 is that swimming pool that ethical hackers can use to learn about ethical hacking without breaking any laws and regulations or the need to use production networks as a lab. Metasploitable 2 is an intentionally vulnerable Linux machine which can be downloaded and setup as a virtual machine in any hypervisor such as VMware Player and Virtual box. In the Metasploitable 2 tutorial we will be setting up the vulnerable Linux machine in VMware Player. In the upcoming tutorials we will be using the Metasploitable 2 vm to practice on and guide you through the process of hacking it using Metasploit on Kali Linux.
Setting up Metasploit on Kali Linux 2016 Rolling
When you’re running the latest version of Kali Linux, currently that is the 2016 rolling edition, you just need to click the Metasploit icon on the dock. This will start the PostrgreSQL service, the Metasploit service and msfconsole automatically. When you launch Metasploit for the first time it will set-up and configure the Metasploit database.
Setting up Metasploit on Kali Linux before 2016 Rolling edition
In order to use Metasploit on any Kali Linux version before 2016.01 Rolling edition you need to do 3 things:
- Start the Kali PostgreSQL service.
- Start the Kali Metasploit service.
- Start the msfconsole.
To start the PostgreSQL service we need to issue the following command in the terminal:
service postgresql start
Then use the following command to start the Metasploit service:
service metasploit start
And the following command to start msfconsole:
msfconsole
Now use the following command to check if there is a database connection:
msf > db_status
If you want to start the PostgreSQL and Metasploit service at boot time you need to edit the update-rc.d by using the following commands:
update-rc.d postgresql enable
update-rc.d metasploit enable
Metasploitable 2 installation and configuration
First we need to download the Metasploitable 2 virtual machine which contains the vulnerable host machine we will be practicing on in the upcoming tutorials. Make sure you have sufficient resources on your host system for installing and running the virtual machine. You need to have at minimum 10 gigabytes of storage space and enough RAM for your host system, the Metasploitable host and Kali linux if you’re running Kali in a VM on the same host. The Metasploitable 2 download is available from Sourceforge using the following link:
After unzipping the downloaded ZIP file you need to open the virtual machine from VMWare Player:
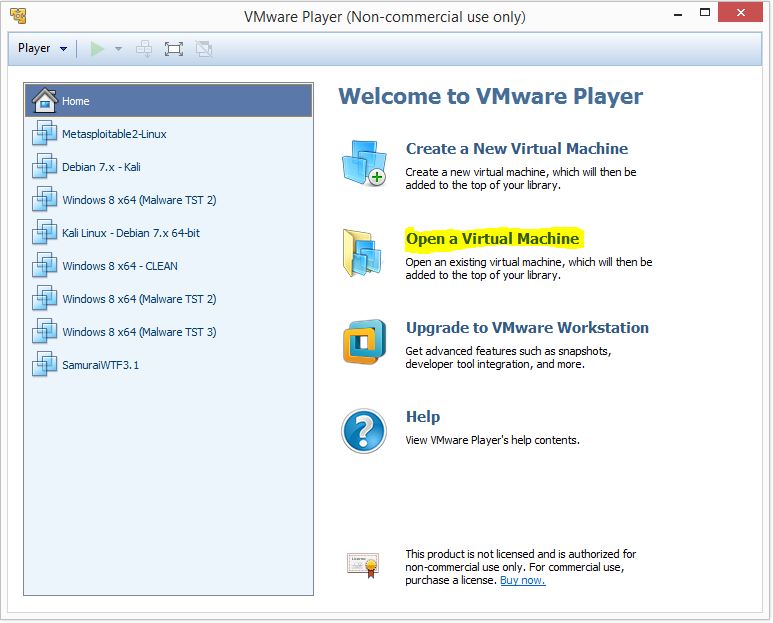
Browse to the folder where you have unzipped the Metasploitable 2 image and add it to your VM list by selecting the .vmx file. The new VM will appear in the list on the left side of the window and is named Metasploitable2-Linux. We do not need to change the Virtual Machine settings so we can start the VM right away by selecting the new VM and click “Play Virtual Machine”:
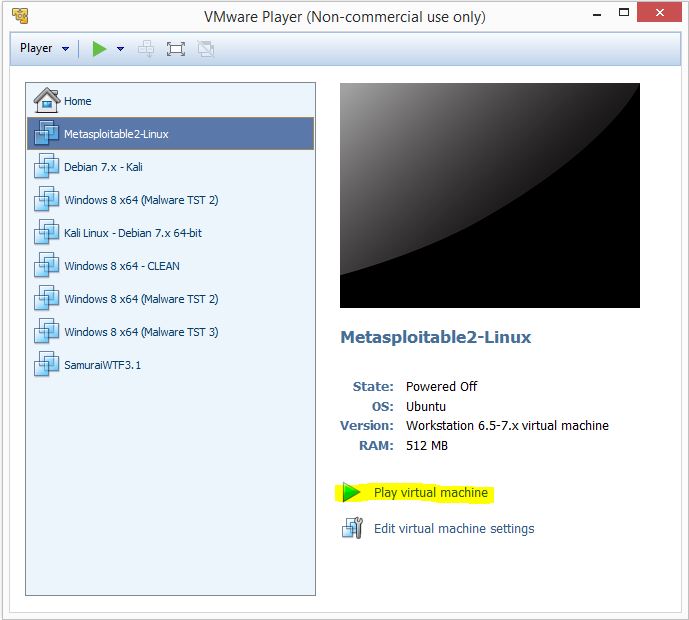
VMWare played might ask you if you have copied or moved the Virtual Machine, click the copied button to continue. Metasploitable 2 will configure itself and present you with a login screen as following:
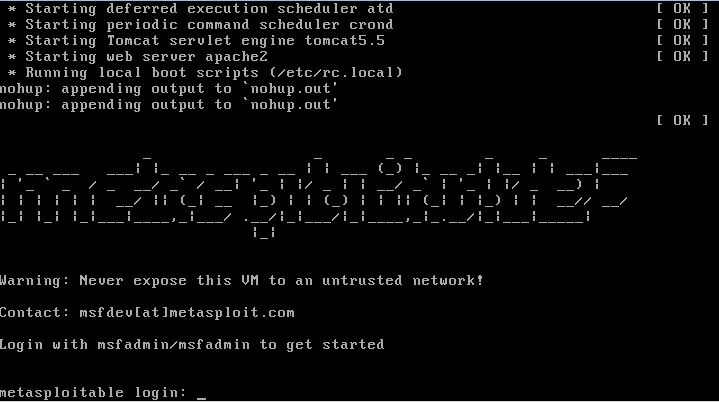
Login to the virtual machine by using the following credentials:
Username: msfadmin
Password: msfadmin

Now that our vulnerable Linux machine is running and we can type the ifconfig command to retrieve the IP address of the Metasploitable 2 virtual machine:
msfadmin@metasploitable:~$ ifconfig
The IP address will appear on the eth0 network adapter as following:
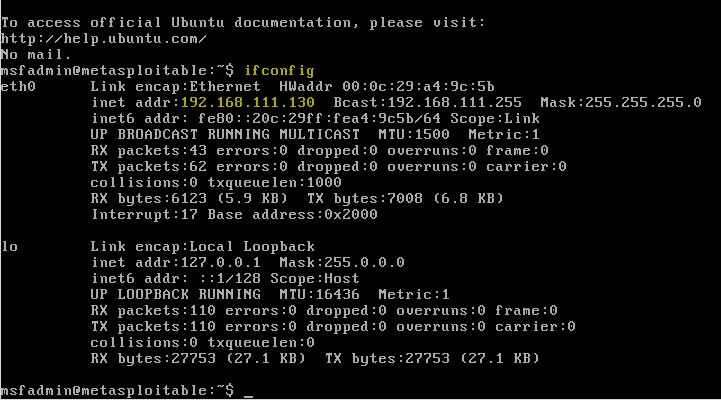
So far we are done with configuring the vulnerable virtual machine and we can switch back to Kali Linux to run some scans on the vulnerable host to determine open ports and running services.
If you are unfamiliar with the Metasploit command line interface and the MSFConsole at this point of the tutorial I recommend you to read the Metasploit basic commands tutorial first before proceeding.
Are you ready to exploit different vulnerabilities and root Metasploitable 2? Follow any of these tutorials: